Read the text and answer question.

The underlined word in line 1 can be replaced by only one of the words below. Choose the right alternative.
On the ideas of the text and the vocabulary used in it, judge the next items.
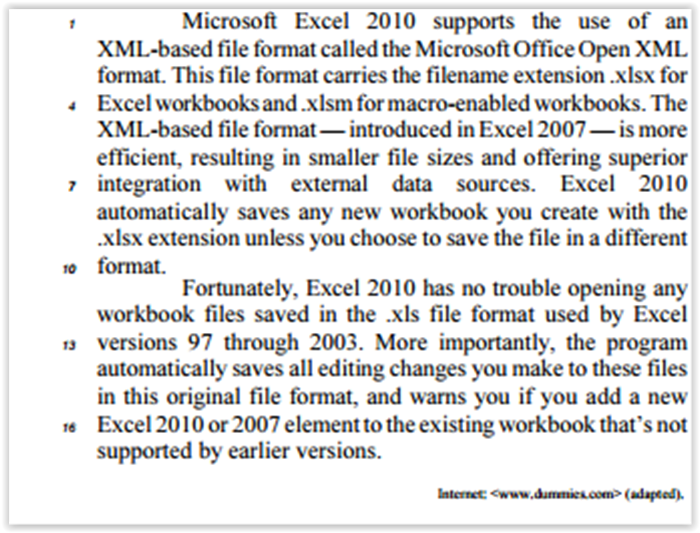
In line 9, “unless” can be correctly replaced by except if.
E-mail Spoofing
E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source. Distributors of spam often use spoofing in an attempt to get recipients to open, and possibly even respond to, their solicitations. Spoofing can be used legitimately. However, spoofing anyone other than yourself is illegal in some jurisdictions.
E-mail spoofing is possible because Simple Mail Transfer Protocol (SMTP), the main protocol used in sending e-mail, does not include an authentication mechanism. Although an SMTP service extension (specified in IETF RFC 2554) allows an SMTP client to negotiate a security level with a mail
server, this precaution is not often taken. If the precaution is not taken, anyone with the requisite knowledge can connect to the server and use it to send messages. To send spoofed e-mail, senders insert commands in headers that will alter message information. It is possible to send a message that
appears to be from anyone, anywhere, saying whatever the sender wants it to say. Thus, someone could send spoofed e-mail that appears to be from you with a message that you didn't write.
Although most spoofed e-mail falls into the “nuisance" category and requires little action other than deletion, the more malicious varieties can cause serious problems and security risks. For example, spoofed e-mail may purport to be from someone in a position of authority, asking for sensitive data, such as passwords, credit card numbers, or other personal information – any of which can be used for a variety of criminal purposes. One type of e-mail spoofing, self- sending spam, involves messages that appear to be both to and from the recipient.
In each of the following text pages, a connective is missing.
I. Six months ago, saving Libya from potential atrocities inspired by Moammar Gadhafi meant establishing a no- fly zone over the country, all the better to protect Benghazi, the rebel stronghold in the east._____________classic mission creep set in and the NATO forces, Canada among them, were bombing Tripoli and clearly trying to eliminate Africas longest-standing dictator and his sons (while denying that was the goal).
II. Like all early civilisations Ancient Greece was an agricultural society. Most of the people lived by farming and the main form of wealth was owning land. In each city there was an upper class and a middle class of men like substantial farmers, doctors and teachers. ____________ the vast majority of people were peasants and craftsmen or slaves. Slavery was common. (It is estimated that about 30% of the population of Athens was made up of slaves). If they worked in rich peoples homes slaves could be reasonably treated. However by law owners were allowed to flog slaves. Those slaves who worked in mines probably suffered the most.
III. Older people are facing a scarcity of qualified nurses to care for them_____________the Government changes its policy on undergraduate education, a leading nursing organisation has warned. The All-Ireland Gerontological Nurses Association (AIGNa) is calling for the urgent introduction of specialised nursing degree courses in care for older people - as an estimated 700 jobs remain unfilled in the sector.
The alternative that respectively brings the correct connective for each one is:
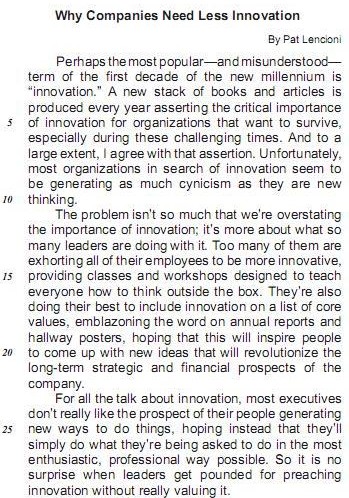
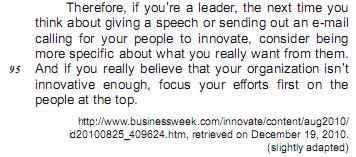
The sentence, in Text I, in which the boldfaced expression introduces an idea of addition is
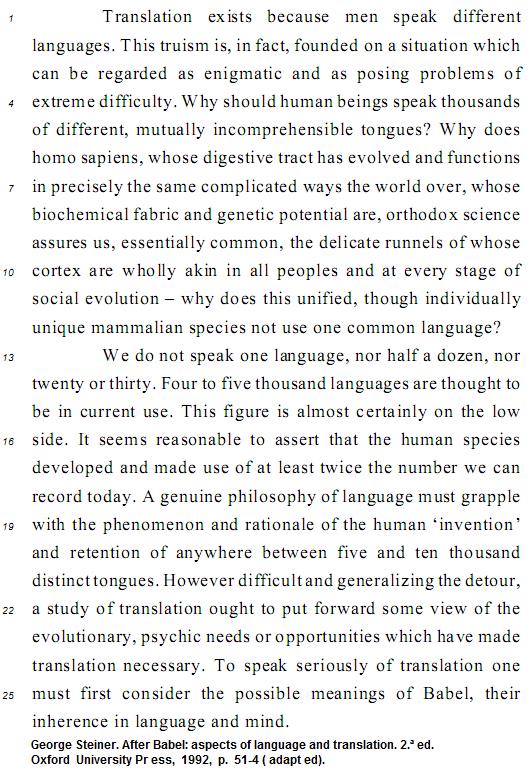
Based on the text, judge the items from 111 to 120.
However (L.21) can be correctly replaced by notwithstanding.
The boldfaced item is synonymous with the expression in parentheses in
The boldfaced item is synonymous with the expression in parentheses in
In The twentieth century has been called the hydrocarbon century due to the abundance of fossil fuels, and their contribution to human development. (lines 1-3), due to can be substituted by:
The match between the discourse marker in boldtype and its communicative intention is expressed in
The linking words in boldtype and the item in parentheses are semantically equivalent in